
After training, only 1.2 per cent were likely to be victims. These trained employees become a “human firewall”, Mitnick said. Still think cybersecurity awareness is a waste of time?
Step 3: Train your users
Next, it’s time to train your users. There are specialist companies who run training exercises but this can also be done in-house. Here are some of the things you should teach your users:
• Learn how to spot a phishing email (more about this below);
• Only click links in email you know for certain are legitimate;
• Do not open or interact with emails from businesses unless you were expecting them. Ignore the message and go directly to the website if worried about the contents;
• Never, EVER, enter your credentials or credit card information on an email. Also make sure you enter your sensitive information on secure websites;
• If by accident you clicked a malicious link or somehow fell under attack by malware, shut down your machine or immediately start a virus scan and get in touch with the IT admin.
Another technique phishers use is to keep sending the same bogus email repeatedly, hoping the victim will eventually fall for it.
Unfortunately, this technique has proved to work. In a recent report by Verizon it was revealed that “running a campaign with just three e-mails gives the attacker a better than 50 percent chance of getting at least one click.
Run that campaign twice and that probability goes up to 80 percent.” The report continued, “sending 10 phishing e-mails approaches the point where most attackers would be able to slap a ‘guaranteed’ sticker on getting a click.”
What the phishing lure looks like
One way to spot a phishing attack is to know what it looks like. Phishing emails will use similar branding to the emulated service but there are certain things you can look out for and Microsoft Security Centre offers the following example.
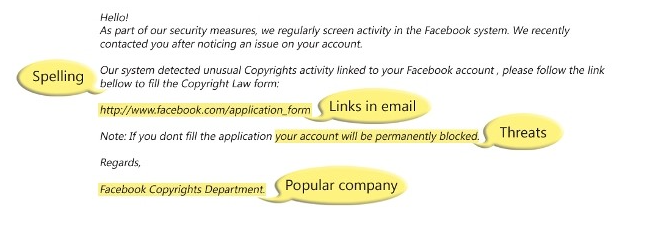
Some items to look for are misspelled words and bad grammar typical of phishing messages from Eastern Europe and China. Phishing emails sometimes include links within the email that look legitimate but really link to bad sites and they either contain threats or promote gifts.
There are other indicators that a trained eye will spot easily. Check the email address of the sender; place the cursor (DO NOT CLICK) over the address and check in the bottom left of your browser where that link is pointing to. You can do the same for links in the body text.
For years, banks and ecommerce sites have implemented clear guidelines on how they contact customers and request information. They don’t ask for your details by email. Simple. If, for example, you use online banking services, any messages will be sent to customers inside that system which most likely uses 2-factor authentication.
One final word of advice you can give to users is “think before you click”. Tell them to take a few extra seconds before opening attachments or clicking on links.
Even better, if they have any doubts, call help and forward that email. If it’s spam, help staff will quarantine the email and add it to their blocklist.
When users start identifying phishing email and passing them on to IT support, you know your message has hit home.
Tools of the anti-phishing trade
Remember, you’re not alone in this fight. There are many tools out there designed to help you get rid of the scourge that is unwanted emails and email attacks.
GFI MailEssentials, for example, does just that by getting rid of 99 per cent of spam messages, and has special anti-phishing features built right in.
By Doug Barney - GFI Software




